Caesar Cipher
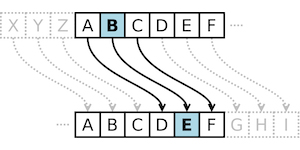
The Caesar Cipher is one of the simplest and most well-known methods of encrypting textual messages. It was named after the Roman emperor Gaius Julius Caesar, who is believed to have used it for communication with military commanders. The Caesar Cipher is based on the straightforward principle of character substitution in a message using an alphabet shift.
The operation of the Caesar Cipher is quite simple: each letter of the alphabet is replaced with another letter a fixed number of positions down or up the alphabet. This number of positions is referred to as the cipher key. For instance, if the cipher key is 3, each letter is replaced with the letter three positions ahead in the alphabet. Thus, "A" becomes "D," "B" becomes "E," "C" becomes "F," and so on.
The simplicity of the Caesar Cipher makes it accessible and understandable even to beginners. However, this cipher is very vulnerable to decryption, especially when using computer programs or analytical methods. Since the alphabet consists of a limited number of characters, there are only 26 possible cipher keys. This means that an attacker can simply try all the possible options to decrypt the message.
Despite its simplicity and low level of security, the Caesar Cipher is still used in various domains, particularly in cryptography education and for recreational purposes. It can serve as an interesting historical example of encryption and stimulate interest in the study of more complex encryption methods.
In conclusion, the Caesar Cipher is a simple historical cipher based on the alphabet shift principle. It was used in ancient times and is still employed today in cryptography education and for recreational purposes. Despite its simplicity, it offers a low level of security and can be easily decrypted. Nevertheless, the Caesar Cipher remains an intriguing example of historical encryption, introducing individuals to the world of ciphers and cryptography.
Comments on the service

A simple substitution cipher for alphabetical writing in which the n-th letter of the alphabet is replaced by the letter m - n + 1.
Go to calculation
A two-letter binary cipher in which alphabet letters are replaced by symbols 'A' and 'B' based on binary coding rules and principles.
Go to calculation
A1Z26 is a simple method of encrypting text in which each letter of the alphabet is assigned a specific number, determined by its number.
Go to calculation